You’ve probably seen this scenario unfold before. Someone in the company clicks a suspicious link. Their password, maybe reused or too simple, gets compromised. Suddenly, systems are exposed, customer data is at risk, and the damage control begins.
What’s so frustrating about this is that a second layer of verification, just one more step, could’ve prevented the whole thing.
Two-factor authentication (2FA) has the power to do that. It’s one of the most effective, low-friction ways to stop unauthorized access and secure your systems. Whether you’re running campaigns, managing customer accounts, or developing tech infrastructure, understanding how 2FA works and implementing it properly stops being optional. Let’s dig in.
What is two‑factor authentication? A 2FA guide for CPaaS users
Two‑factor authentication is often dismissed as something only security experts worry about. But it’s quickly becoming an essential means for protecting business-critical operations, especially when your platform touches customer data or sensitive workflows.
And yet, many teams still treat it as nonobligatory. Let’s fix this flawed assumption, starting with a clear definition and a look at how it functions in real-world environments.
Definition of two‑factor authentication
Two-factor authentication system is a security mechanism that requires users to provide two distinct forms of verification before gaining access to an account or system. In other words: just a password isn’t enough.
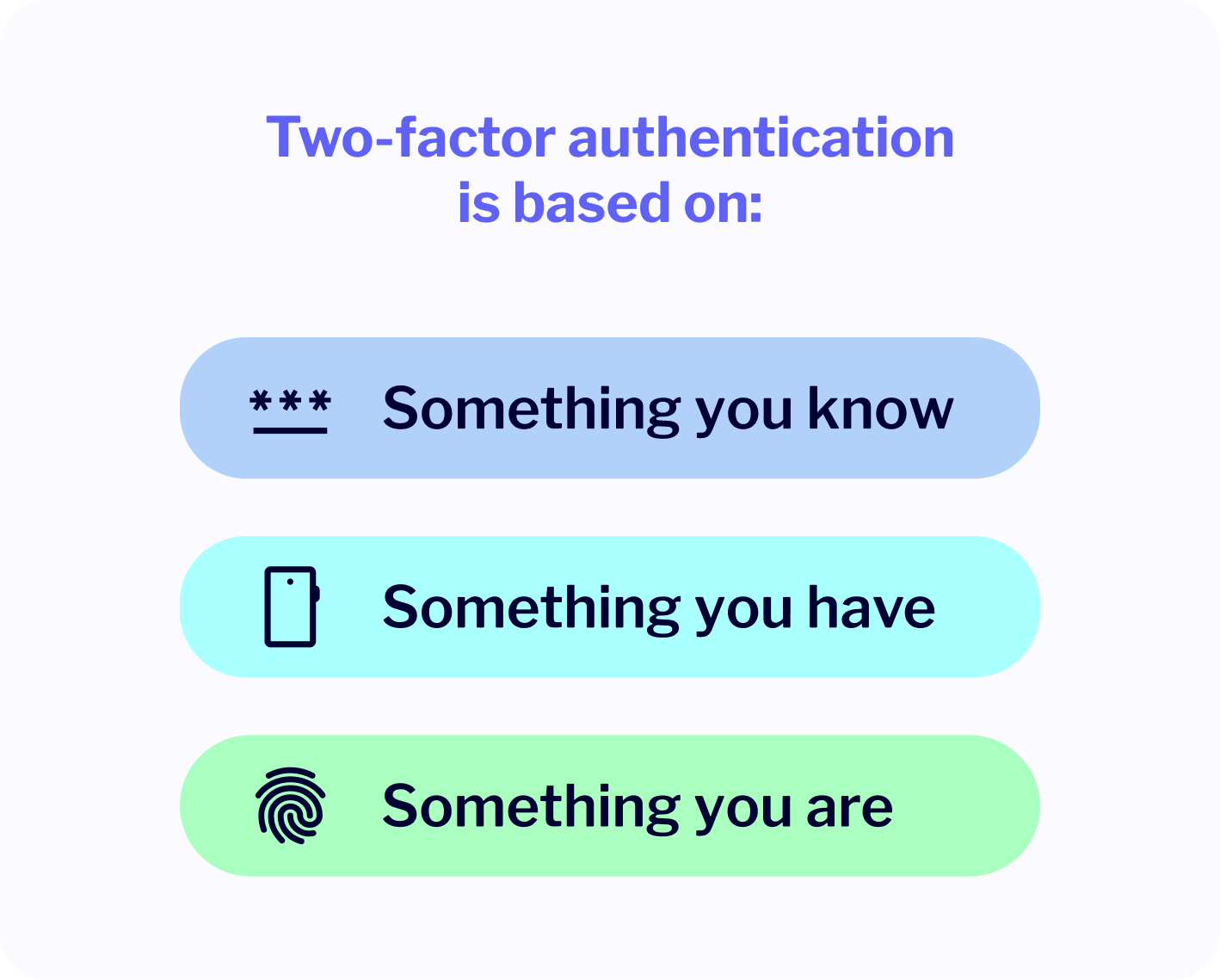
The authentication factors typically fall into different categories:
- Something you know (e.g., a password or PIN)
- Something you have (e.g., a phone or hardware token)
- Something you are (e.g., a fingerprint or face scan)
Why does this matter? Because even if one factor gets exposed in a breach, an attacker still needs the second factor to get in. That second step creates a speed bump that most automated or opportunistic attacks can’t get past.
To put it another way, if a password is a key, 2FA adds a second lock on the door, and this second lock changes every 30 seconds.
How two‑factor authentication works in practice
Let’s break this down with an example most of us have encountered.
You’re logging into your app’s or tool’s dashboard. You enter your email and password – so far, so good. But instead of immediate access, you’re prompted to verify a code sent to your phone. You open your authenticator app or SMS, grab the six-digit code, and punch it in.
Done. You’re in. That’s 2FA at its most basic:
- You authenticate with something you know (your password).
- You confirm your identity with something you have (a device or token).
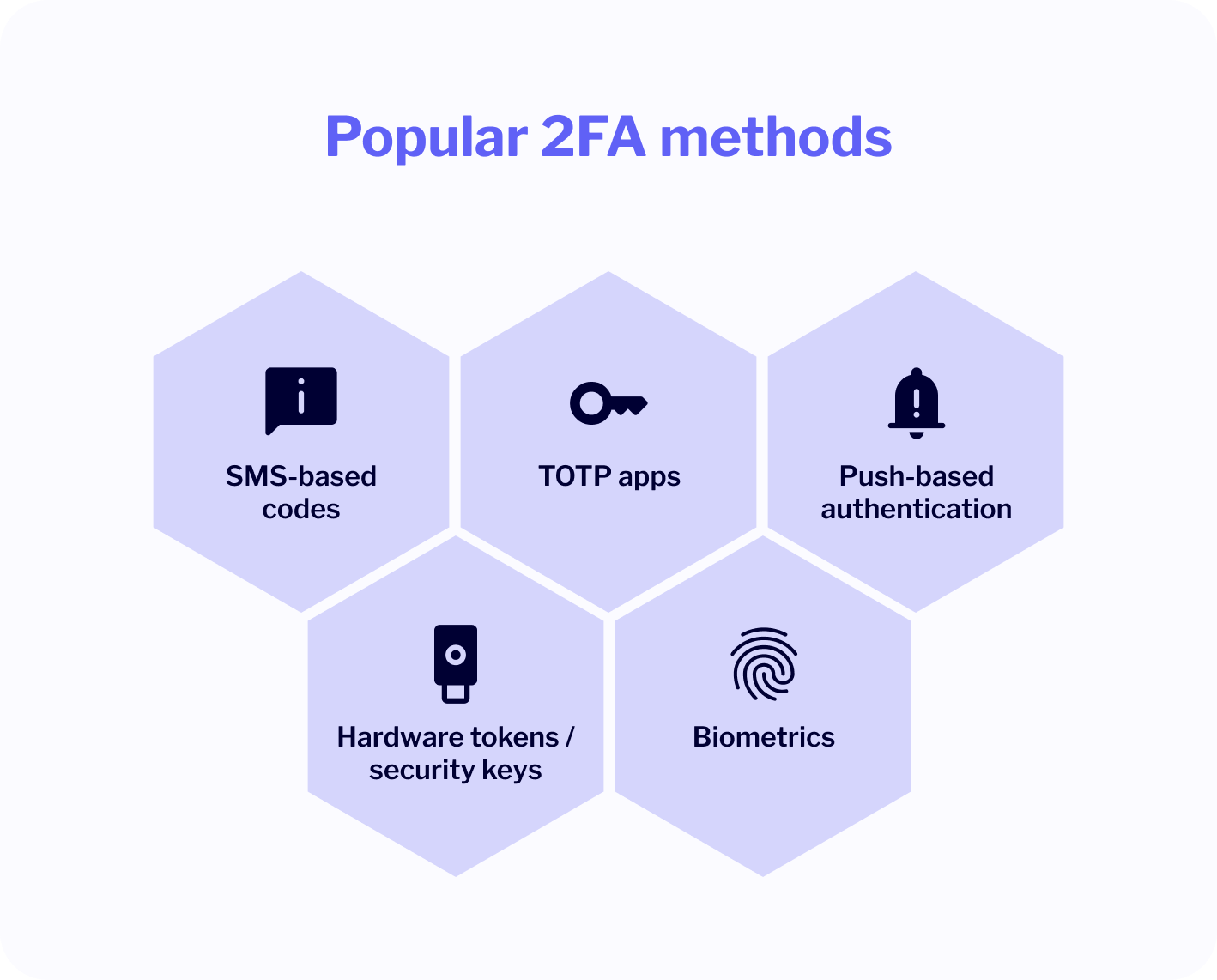
Here are the most common forms of 2FA you’ll encounter:
- SMS-based codes: A one-time password (OTP) sent to your phone via text. Easy to set up, but vulnerable to SIM swapping and phishing attacks.
- TOTP apps: Apps like Google Authenticator or Microsoft Authenticator generate time-based OTPs. These codes expire quickly and don’t require an internet connection.
- Push-based authentication: You get a notification on your phone asking you to approve or deny the login attempt. This is common with Duo or Okta.
- Hardware tokens / security keys: Physical devices like YubiKeys that plug into your USB port or connect via NFC. These offer the highest security with minimal user input.
- Biometrics: Face ID, fingerprint scans, or retina recognition, usually baked into your phone or laptop as a third layer or fallback.
Each method has its pros and trade-offs. A text message is user-friendly but more vulnerable. Authenticator apps strike a solid balance between ease of use and greater security. Hardware keys are nearly bulletproof but can be lost or misplaced. Choosing the right one often depends on your risk profile and user base.
The best 2FA setup is the one people actually use. If adoption is low due to friction, even the most secure method won’t help. Thus, we encourage our users to start with TOTP apps – they’re secure, mobile, and familiar.
The point is, 2FA isn’t some obscure technical process. It’s a straightforward, proven way to protect the integrity of your platform, your customer data, and your brand’s reputation. And as we’ll explore in the next sections, the numbers make a pretty compelling case too.
Why use two factor authentication? Key security benefits
We live in a world where attackers don’t need to break down your digital front door – they just wait for you to forget to lock it. The simplest way in is still the most common: username and password. They’re often weak, reused, or exposed in breaches without anyone realizing. This is where two‑factor authentication proves its worth.
Let’s break down exactly how 2FA strengthens your defenses, using real-world examples and clear, business-relevant advantages.
Preventing account takeover and phishing
Phishing has evolved. Attackers don’t just send awkward emails anymore – they craft smart, convincing messages that appear to come from internal departments, trusted apps, or even team members. All it takes is one person clicking the wrong link and typing in their credentials.
And when that happens, without 2FA, the attacker walks right in.
With 2FA in place, the attacker might have the correct login, but they hit a wall when they’re prompted for a time-based code or a device confirmation. No phone? No authentication token? No access.
Case in point: Google rolled out mandatory 2FA for over 150 million users and saw a 50% drop in account compromises almost immediately. It’s not a silver bullet, but it turns phishing from a one-click catastrophe into a dead end.
Takeaway: Even if your password is stolen, two-factor authentication dramatically lowers the risk of a successful breach, especially in social engineering attacks where human error is involved.
Blocking credential stuffing and password reuse exploits
Here’s the elephant in the room: people reuse passwords. A lot.
Credential stuffing attacks, where hackers take known username-password combos from previous breaches and try them en masse on other services, are ridiculously common. There are bots designed to do nothing else.
According to Verizon’s Data Breach Investigations Report, over 80% of hacking-related breaches involve weak or stolen credentials. Once those are out in the wild, your platform becomes a target, especially if users tend to repeat passwords across services.
With 2FA on, even if a reused password gets cracked, it’s not enough. The attacker still needs that second factor to complete the login. Without it, the credential stuffing attempt fails.
Real-world example: In one documented case, Basecamp logged over 30,000 automated login attempts in a single hour ultimately compromising 124 user accounts before additional rate limiting and CAPTCHA protections were enforced. That’s a stark reminder of how devastating credential stuffing can be in just 60 minutes.
Takeaway: Two-factor authentication neutralizes one of the most common breach tactics – password recycling. It makes credential stuffing a waste of time.
Regulatory and compliance advantages for businesses
Keeping bad actors out is one thing, but security these days is also about staying compliant.
Whether you’re subject to GDPR, HIPAA, SOC 2, or ISO/IEC 27001, implementing multifactor authentication (MFA), including 2FA, is either strongly recommended or flat-out required for handling sensitive data and systems.
In many B2B contexts, especially when serving enterprise clients or public institutions, 2FA becomes a baseline expectation.
Why it matters for your team:
- Reduces liability in the case of a breach.
- Strengthens your security posture during audits.
- Demonstrates seriousness about data protection to prospects and partners.
Takeaway: Implementing 2FA helps your risk reduction efforts and constitutes a reputational and legal safeguard. The sooner you standardize it across your stack, the better your position when scrutiny comes knocking.
Two‑factor authentication adoption and risk statistics
The data is clear: while 2FA (or MFA) offers outstanding protection, adoption rates, especially among SMBs and non-tech industries, are still lagging.
Current 2FA / MFA adoption rates across enterprises and SMBs
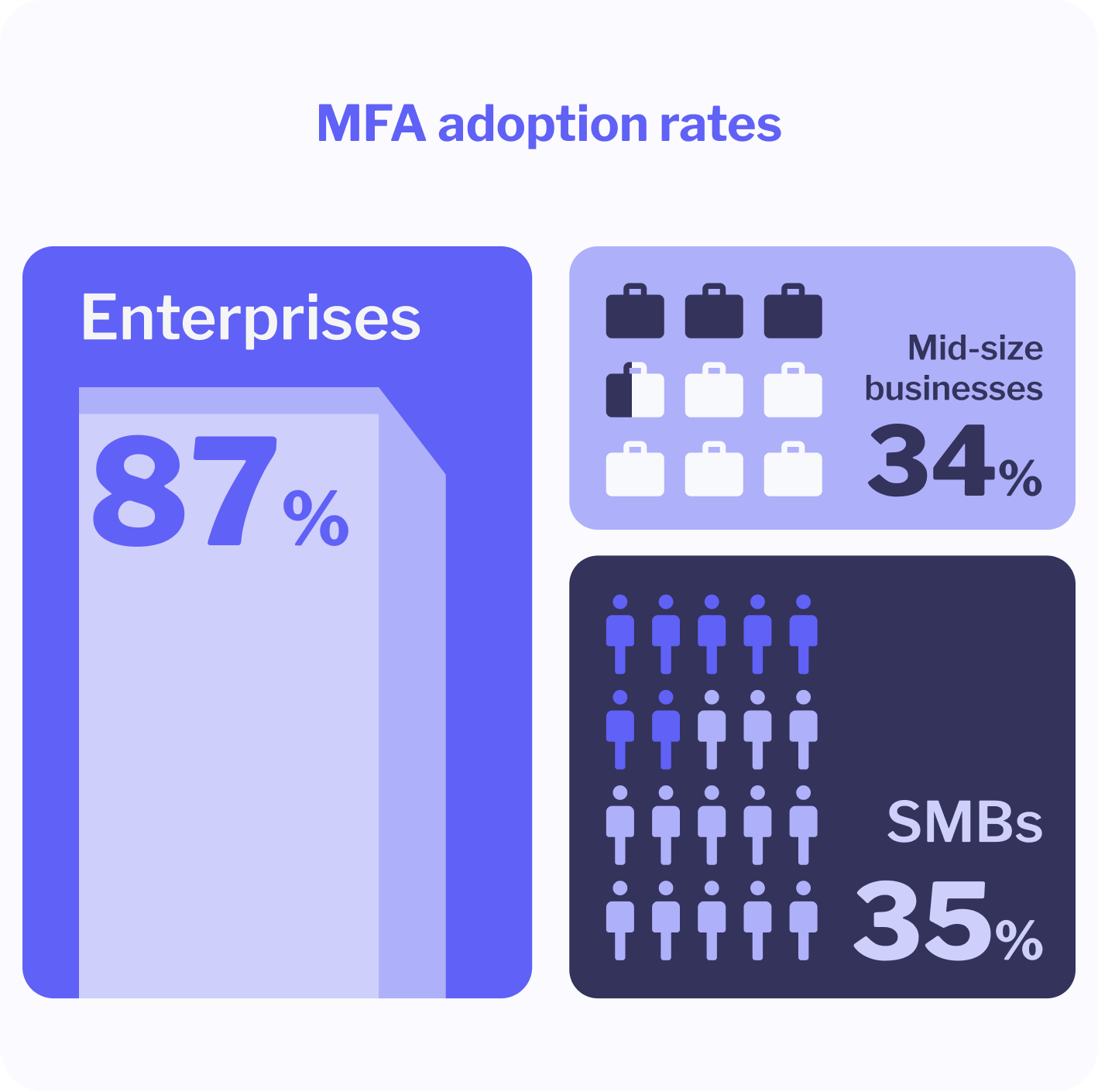
- Among enterprises with more than 10,000 employees, 87% have deployed MFA as a standard layer of security. Tech companies lead this trend, while small and mid-sized businesses remain behind.
- In mid-sized firms with 26–100 employees, only about 34% use MFA. For small firms (1–25 employees), that drops to 27%.
- Nearly 65% of global SMBs report not using MFA at all, with 58% unaware of its security benefits, and only 17% have internal policies requiring it.
Takeaway: MFA is now mainstream in larger enterprises but remains an often-overlooked minimum standard in the SMB segment even though their risk exposure is just as real.
Consequences of weak or no 2FA
- Over 80% of breaches involve weak, stolen, or reused credentials, illustrating how easily password-based security systems are manipulated.
- When account credentials are available, credential stuffing and phishing become high-efficiency attack vectors. In one case, 23andMe experienced a breach where reused credentials exposed around 5.5 million user records, driven in part by lack of 2FA and controls like rate limiting.
Takeaway: Organizations that ignore 2FA not only expose themselves to breach risk – they risk brand damage, compliance fallout, and costly operational disruptions.
Real‑world effectiveness figures
- Microsoft reports that MFA, when properly configured, blocks over 99.9% of automated account compromise attempts.
- Independent research confirms MFA can reduce breach risk by 99.22% across general populations, and 98.56% of account compromise risk remains mitigated even with leaked credentials.
- Some reports suggest MFA adoption (incorrectly for cloud users) is as low as 11%, with over 99.9% of successful compromises occurring on unprotected accounts.
Takeaway: With numbers like these, 2FA is less a precaution and more a proven security imperative. When enabled, the vast majority of credential-based attacks simply can’t succeed.
Types of two‑factor authentication methods
Two-factor authentication doesn’t involve a single, standardized approach. There are multiple ways to implement 2FA, each with its own pros, trade-offs, and levels of protection. The key is finding authentication protocols that align with your users’ habits and your organization’s risk profile.
Let’s explore the most widely used types of 2FA – from the most common to the most robust – so you can make informed decisions about how to layer your defenses.
SMS-based codes (OTP via SMS)
This is often where people start with 2FA, and for good reason. It’s simple, familiar, and doesn’t require installing anything. You enter your password, and a one-time code (OTP) is sent to your phone via text. Type in the code, and you’re in.
Why it’s popular:
- No learning curve.
- Works on virtually any mobile phone.
- Quick to deploy across a large user base.
But there’s a catch.
SMS is notoriously vulnerable to SIM-swapping attacks, phone number porting fraud, and phishing. An attacker who social engineers your mobile carrier can intercept your messages and access your accounts.
✅ Use it if: You need a lightweight option to get people started.
🚫 Avoid it if: You’re protecting admin dashboards, finance tools, or sensitive customer data.
Authenticator apps / TOTP
These apps generate Time-Based One-Time Passwords (TOTP) – usually six-digit codes that refresh every 30 seconds. Google Authenticator, Microsoft Authenticator, and Proton Authenticator are the big players here.
Unlike SMS, TOTP codes are not transmitted over the network. They’re generated locally on your device, making them more resistant to interception or phishing.
Why it works:
- Offline capable.
- Time-sensitive codes reduce reuse risk.
- Much harder to phish than SMS.
✅ Use it if: You want increased security and a better UX than SMS, without going full enterprise.
🚫 Avoid it if: You’re managing a user base that might struggle with installing or maintaining an app.
Push notification / mobile app approval
This method sends a prompt to your phone asking you to approve or deny an authentication attempt. Duo, Okta Verify, and Microsoft Authenticator all offer this experience.
It’s arguably the most convenient form of 2FA: no code to copy, just tap “Approve.” Some apps even display login metadata (like IP address or device) to help you verify legitimacy.
Why it’s great:
- Frictionless UX.
- Often includes context-aware security (e.g., location, device fingerprint).
- Easier adoption at scale.
✅ Use it if: You want high adoption and a smooth user experience.
🚫 Avoid it if: You’re protecting highly sensitive systems and want more deliberate friction.
Hardware security keys / FIDO U2F & passkeys
This is where things get truly locked down. Hardware security keys, like YubiKey or SoloKey, use physical devices to verify identity. You plug the key into your computer (USB, NFC, or Bluetooth), tap it, and get verified.
They’re built on FIDO U2F (Universal 2nd Factor) or the newer FIDO2/WebAuthn protocols, which include passkeys – passwordless login options backed by public-key cryptography and platform biometrics (Face ID, Windows Hello, etc.).
Why it’s ironclad:
- Immune to phishing (no codes to intercept).
- Tied to specific devices, making impersonation nearly impossible.
- Fast and seamless in most environments.
Downsides:
- Requires physical distribution and backup management.
- Slightly more technical onboarding.
- Lose the key? Recovery depends on backup protocols you’ve set.
✅ Use it if: You’re securing admin access, production environments, or handling high-value data.
🚫 Avoid it if: Your users aren’t ready to manage physical security tokens.
Backup codes & recovery options
Even the best 2FA system needs a fallback. That’s where backup codes and recovery methods come in.
Most platforms let you generate a set of one-time-use backup codes during setup. These can be printed, stored offline, or saved in a password manager. They’re your last resort when you lose your device or switch phones.
Key reminders:
- Never store backup codes alongside your main credentials.
- Reissue codes if they’ve been exposed.
- Communicate clearly to users where to find or regenerate them.
Some services also offer alternative recovery methods like:
- Email-based reauthentication (less secure).
- Security questions (generally discouraged).
- Contacting support for identity verification.
✅ Use it if: You want users to avoid getting locked out.
🚫 Avoid relying on it as: Your main line of defense – these are emergency tools only.
When to use 2FA? Implementation scenarios for CPaaS
Two‑factor authentication becomes even more critical when your platform acts as the backbone of digital communication – think CPaaS (Communications Platform as a Service). In this environment, one compromised login can give bad actors access to sensitive messaging data, campaign workflows, or even customer contact lists.
That’s why it’s not enough to just have 2FA available. You need to implement it in the right places, tailored to how your users, whether internal or external, interact with the system.
Let’s look at four high-priority use cases where 2FA makes a tangible difference in the CPaaS world.
End-user account protection
If the platform provides self-service dashboards or analytics portals to customers, enabling 2FA for those accounts should be a standard practice.
Think of a marketing manager logging in to schedule SMS or push campaigns. If someone else gains access to that account, even briefly, they could send spam to thousands of recipients, leak personal data, or wreak havoc with your customer’s sender reputation.
Key risks reduced by 2FA here:
- Unauthorized campaign launches.
- Data exports and contact list theft.
- Damage to brand trust (theirs and yours).